| |
-
-
UEFI and Legacy BIOS
UEFI Specification
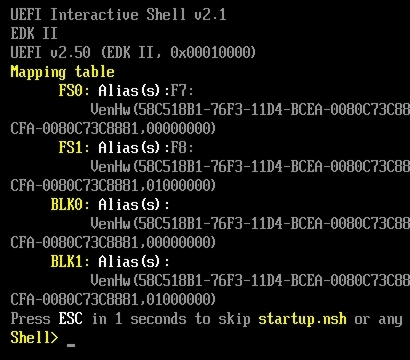
UEFI Shell
Shell Script
Memory Layout (SMRAM and Memory Map)
UEFI GUID Interface
Services and Protocols
UEFI Application Development
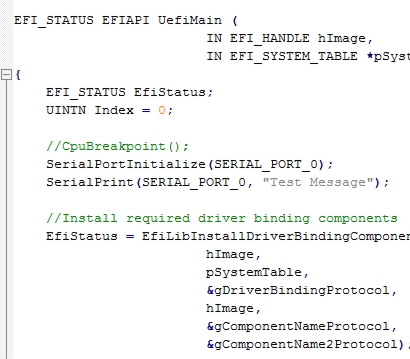
EDK-II Development Environment
Development with Visual Studio
OVMF with QEMU and TIANOCORE
UEFI Debugging
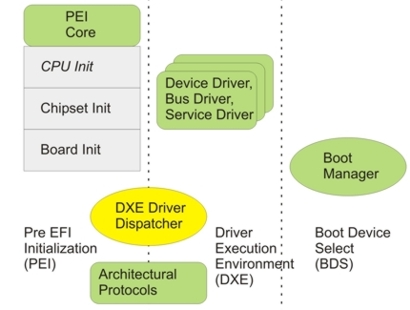
UEFI DXE Driver
Resource Management
UEFI PCI resource management
Post-DXE Management
Runtime Driver
SMM Management
SMM Driver
Data Storage
Secure Boot and Key Management
UEFI Driver Signing
-
|
|
|
|
UEFI Shell
|
| |
EDK-II |
|
|
|
Knowledge of C programming is required for the course
|
| |
The training is offered as "Hybrid Training" (remote or classic). Sybera also offers this training as an in-house seminar at the customer's location
|

|
Expert Course: UEFI Firmware Development
|
|
The UEFI Firmware Training is a comprehensive, practical seminar on the development of modern firmware software based on the Unified Extensible Firmware Interface (UEFI). The course is offered as a hybrid training, allowing participants to join remotely or on-site, and is ideal for developers who want to deepen their knowledge in firmware development. UEFI replaces the traditional BIOS with a standardized interface that provides boot and runtime services, enabling firmware development for modern systems.
|
Goal of the Training
|
|
The goal of the UEFI training is to provide developers with a fundamental understanding of the UEFI architecture and specification and to enable them to professionally implement their own firmware projects. The course covers the relevant UEFI phases, Shell concepts, services, and protocols, and practically demonstrates how developers can create and debug firmware software, including their own drivers (DXE drivers). This gives participants the necessary skills to develop sophisticated firmware solutions for modern CPU platforms.
|
Training Content
|
|
The training covers the fundamentals of UEFI and Legacy BIOS, the UEFI Specification, the interactive UEFI Shell with scripting capabilities, as well as the Memory Layout and GUID Interfaces. The program includes UEFI application development, use of the EDK-II Development Environment, integration with Visual Studio, working with OVMF and QEMU, and UEFI debugging. Further training content includes the development of UEFI DXE drivers, resource and PCI management, Post-DXE phases, runtime drivers, SMM Management, data storage, Secure Boot concepts and driver signing.
|
Who is the Training Suitable for?
|
|
The UEFI Firmware Training is aimed at hardware and software developers who need to implement their own firmware projects or supplement existing UEFI processes. Prerequisites for participation are solid knowledge of C programming, as this is essential for implementing the practical training content and developing custom firmware components. The course offers a deep dive into UEFI and is ideal for developers who want to develop professional CPU platforms.
|
Course Formats
|
The training is offered in a hybrid format: remote, in-person, or in-house at the customer's location, allowing for flexible learning regardless of location. In-person courses at Sybera offer an interactive environment and exchange with other participants. In-house training can also be individually tailored to company projects and specific requirements.
|

